Versions Compared
Key
- This line was added.
- This line was removed.
- Formatting was changed.
| Div | ||||||
|---|---|---|---|---|---|---|
| ||||||
In This Article
|
Overview
Granular Delegated Admin Permissions (GDAP) is Microsoft's new security and compliance capabilities for Microsoft CSP partners like Evolve IP. GDAP allows you to define the level of access a CSP partner has to your 365 tenant. Microsoft's introduction of GDAP means you no longer need to give a CSP partner global admin permissions in your 365 tenant. Instead, you work with your CSP partner to configure time-limited access rights (using Azure AD roles) in your 365 tenant.
In addition, GDAP comes with extended visibility and granular activity logs that illustrate when GDAP permissions are being used along with the lifecycle of the GDAP relationship.
| Info |
|---|
NOTE Establishing a GDAP relationship with Evolve IP is optional. If you do not require any level of support and only want us to provide O365/M365 subscription products, you can opt out of the GDAP relationship process. However, we will not be able to open any Microsoft Premier support tickets on your behalf. You will be responsible for opening support tickets with Microsoft. |
GDAP Relationship Details
A GDAP relationship has 2 configuration items:
- The level of access to your 365 tenant, which is configured by selecting one or more Azure AD Roles
- A time limitation (in days) for the access to your 365 tenant
Additional GDAP Relationship Details
- You can have multiple GDAP relationship configurations with Evolve IP, and any other Microsoft CSP partners.
- Each GDAP relationship is time limited. The max is 2 years (730 days).
- A GDAP relationship will automatically expire when the duration (max 2 years) has completed.
- Before expiration, email notifications will be sent 30 days, 7 days, and 1 day before the GDAP expiration date. Emails are sent to your global administrators.
- Due to security reasons, Microsoft does not support a renewal process. A new GDAP relationship must be created to replace the old one.
- You can terminate a GDAP relationship in your Microsoft 365 Admin Center at any time.
- Evolve IP can also terminate a GDAP relationship at any time.
| Info |
|---|
NOTE In the GDAP model, some permissions within an Azure AD role may be limited by Microsoft. In other words, not all tasks within an Azure AD role can be performed with a GDAP relationship. Details on those limitations can be found in Microsoft's Workloads Supported by GDAP article. Additionally, GDAP is not a replacement for having a dedicated user account for Evolve IP to use in your 365 tenant. There may be situations where a dedicated user account in your 365 tenant is required. However, a GDAP relationship should be the preferred method of access, and should always be configured regardless of whether a user account is created for Evolve IP to use in your 365 tenant. |
GDAP Relationship Setup
Here's an overview of the GDAP relationship setup process:
- You work with the Evolve IP Service Delivery or Support teams to determine:
- The level of access to your 365 tenant by selecting one or more Azure AD Roles.
- The time limitation (in days) for the access. There's a minimum of 1 day and a maximum of 730 days (2 years).
- We give you a link to your Microsoft 365 Admin Center that specifies the level of access and the time limitation for the GDAP relationship.
- You click the link, and sign into your Microsoft 365 Admin Center with a user account that's a Global Administrator.
- After signing in, you review and approve the level of access and duration of the GDAP relationship request.
| Info |
|---|
NOTE You can request more than one GDAP relationship, each with their own level of access and time limitation. |
Minimum Level of Access
To give the Evolve IP Service Delivery & Support teams the ability to open Microsoft Premier support tickets on your behalf we require you to approve the below Azure AD Roles, which provides us with the access we need to open support tickets. The GDAP relationship duration should be the maximum 2 years, but if you prefer to make it shorter, that's okay with us.
Global Administrator Access
To provide support and troubleshooting for all of your 365 services the path of least resistance is to provide Evolve IP the Global Administrator role. Here are some things to consider:
- Evolve IP will have the ability to access, view and configure your 365 services including your Azure AD.
- If Microsoft restricts our access to certain 365 services in your tenant, we may request a dedicated user account in your 365 tenant for us to use.
- Even though the global administrator role is granted to Evolve IP, Microsoft does restrict access to view and export certain datasets in your 365 tenant.
| Info |
|---|
NOTE In the GDAP model, some permissions within an Azure AD role may be limited by Microsoft. In other words, not all tasks within an Azure AD role can be performed with a GDAP relationship. Details on those limitations can be found in Microsoft's Workloads Supported by GDAP article. |
Supporting Teams Voice & Direct Routing
The following Azure AD Roles can be selected for a GDAP relationship when supporting an existing Teams Direct Routing configuration:
- Teams Communications Administrator: This role is required for creating, managing, and viewing a Teams direct routing configuration, and for provisioning, or deprovisioning, direct routing users. This role is also used to manage Teams voice policies, call queues, and auto attendants.
- Teams Devices Administrator: Optional role to configure and manage Teams enabled devices (desk phones, conference room devices, etc.).
- Teams Administrator: Optional role used to manage all aspects of a Teams environment including the management of a Teams direct routing configuration. This role is required to manage Teams IP Phone policies.
- User Administrator: Optional role for creating and managing Azure AD users including user account license assignments & blocking user account sign ins. This role does not have the permissions to manage MFA, or to create, modify, or disable user accounts in a local Active Directory that is synced to Azure AD.
| Info |
|---|
NOTE In the GDAP model, some permissions within an Azure AD role may be limited by Microsoft. In other words, not all tasks within an Azure AD role can be performed with a GDAP relationship. Details on those limitations can be found in Microsoft's Workloads Supported by GDAP article. |
Supporting Other 365 Services
Here's a table defining some additional Azure AD Roles that can be configured in a GDAP relationship:.
| Info |
|---|
NOTE Each role listed in the below table is linked directly the role's description and full details in Microsoft's Azure AD Built-In Roles article. |
| Azure AD Role | Description |
|---|---|
| Exchange Administrator | Provides global admin permissions within Microsoft Exchange Online, and has the ability to create and manage all Microsoft 365 groups, manage support tickets, and monitor service health. |
| SharePoint Administrator | Provides global admin permissions within Microsoft SharePoint Online, as well as the ability to create and manage all Microsoft 365 groups, manage support tickets, and monitor service health. |
| Intune Administrator | Provides global admin permissions within Microsoft Intune Online. Additionally, this role contains the ability to manage users and devices in order to associate policy, as well as create and manage groups. |
| Application Administrator | Can create and manage all aspects of enterprise applications, application registrations, and application proxy settings. |
| Billing Administrator | Manages subscriptions, manages support tickets, and monitors service health. |
| Security Administrator | Provides permissions to manage security-related features in the Microsoft 365 Defender portal, Azure AD Identity Protection, Azure AD Authentication, Azure Information Protection, and Office 365 Security & Compliance Center. |
| Conditional Access Administrator | Manage Azure Active Directory Conditional Access settings. |
| Security Reader | Global read-only access on security-related feature, including all information in Microsoft 365 security center, Azure Active Directory, Identity Protection, Privileged Identity Management, as well as the ability to read Azure Active Directory sign-in reports and audit logs, and in Office 365 Security & Compliance Center. |
| Compliance Administrator | Manage compliance-related features in the Microsoft Purview compliance portal, Microsoft 365 admin center, Azure, and Office 365 Security & Compliance Center. Can also manage all features within the Exchange admin center and create support tickets for Azure and Microsoft 365. |
| Domain Name Administrator | Manage (read, add, verify, update, and delete) domain names. |
| Authentication Administrator | Provides permissions to reset authentication methods (including passwords) for non-administrators and some roles. |
| User Administrator | Provides permissions for creating and managing Azure AD users including user account license assignments & blocking user account sign ins. Cannot manage MFA. |
| Helpdesk Administrator | Change passwords, invalidate refresh tokens, create and manage support requests with Microsoft for Azure and Microsoft 365 services, and monitor service health. |
| Licensing Administrator | Can add, remove, and update license assignments on users, groups (using group-based licensing), and manage the usage location on users. |
| Groups Administrator | Manage all groups in the organization across various workloads like Teams, SharePoint, Yammer in addition to Outlook. |
| Windows Update Administrator | Provides permissions to create and manage all aspects of Windows Update deployments through the Windows Update for Business deployment service. |
| Reports Reader | Can view usage reporting data and the reports dashboard in Microsoft 365 admin center. |
| Info |
|---|
NOTE In the GDAP model, some permissions within an Azure AD role may be limited by Microsoft. In other words, not all tasks within an Azure AD role can be performed with a GDAP relationship. Details on those limitations can be found in Microsoft's Workloads Supported by GDAP article. |
Accepting a GDAP Relationship
The following section covers the requirements and the process for accepting a GDAP relationship.
| Info |
|---|
NOTE Upon the GDAP relationship being established, all user accounts assigned the Global Administrator role in your 365 tenant will be notified by email of the new GDAP relationship. |
GDAP Relationship Requirements
- A user account in your 365 tenant assigned the Global Administrator role.
- A unique configuration URL provided by Evolve IP to start the GDAP relationship process
GDAP Relationship Process
- Open a private/incognito browser window (Microsoft Edge is recommended)
- Paste in the configuration URL provided by the Evolve IP Service Delivery or Support teams
- Sign into your 365 tenant with a user account assigned the Global Administrator role
- Review and approve the GDAP relationship (see example screenshot below)
- Confirm the GDAP relationship (see example screenshot below)
| Info |
|---|
NOTE Upon the GDAP relationship being established, all user accounts assigned the Global Administrator role will be notified by email of the new GDAP relationship. |
Managing an Existing GDAP Relationship
To view and manage a GDAP relationship you must sign into your 365 tenant with a user account assigned the Global Administrator role.
- Sign into your Microsoft 365 Admin Center: https://admin.microsoft.com
- Browse to: Settings > Partner Relationships
- All of your GDAP relationships are listed by partner in the Granular Delegated Administrative Privileges (GDAP) section
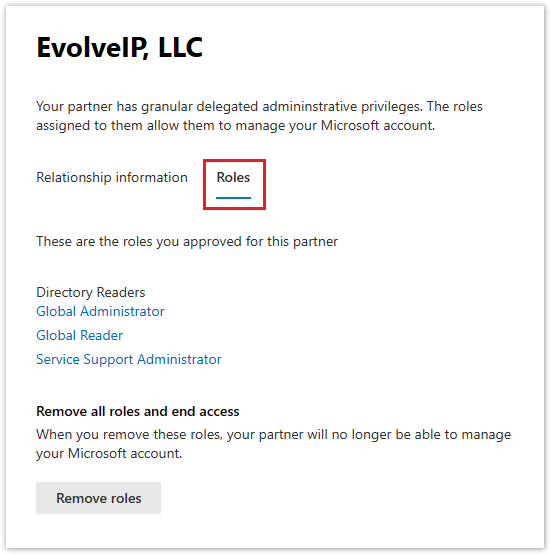
- To view the details of a GDAP relationship, click on the relationship's name (see example screenshot below)
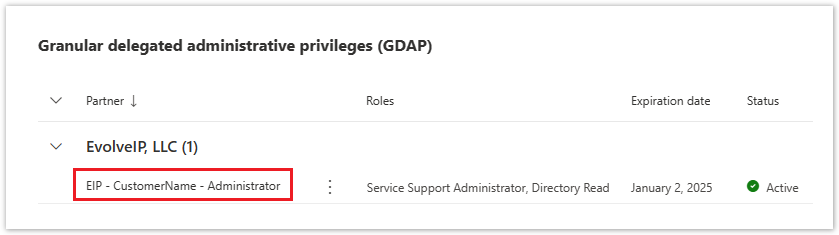
- To remove a GDAP relationship, select the Roles (tab), and click the Remove Roles button
- An email notification will be sent to Evolve IP and all of the global admin user accounts in your 365 tenant
Frequently Asked Questions
| Expand | ||
|---|---|---|
| ||
Establishing a GDAP relationship with Evolve IP is optional. If you do not require any level of support and only want us to provide O365/M365 subscription products, you can opt out of the GDAP relationship process. However, we will not be able to open any Microsoft Premier support tickets on your behalf. You will be responsible for opening support tickets with Microsoft. |
| Expand | ||
|---|---|---|
| ||
The duration of a GDAP relationship can be as little as 1 day, and up to a maximum of 2 years. |
| Expand | ||
|---|---|---|
| ||
Yes. You can have multiple GDAP relationships with their own level of access and duration. You can also have GDAP relationships with multiple CSP partners. |
| Expand | ||
|---|---|---|
| ||
No. Microsoft does not allow this. Your GDAP relationships must have a duration of 1-720 days (2 years). |
| Expand | ||
|---|---|---|
| ||
No. There is no auto-renewal process. Microsoft does not allow this for security reasons. When an existing GDAP relationship is going to expire, a new GDAP relationship must be configured and approved. |
| Expand | ||
|---|---|---|
| ||
Yes. Microsoft sends email notifications to user accounts assigned the Global Administrator role. Notifications are sent out 30 days, 7 days, and 1 day before the GDAP expiration date. |
| Expand | ||
|---|---|---|
| ||
No. There's no change to your existing subscriptions when a GDAP relationship expires. |