- Created by John Dougherty on Jan 04, 2021
You are viewing an old version of this page. View the current version.
Compare with Current View Page History
Version 1 Current »
In This Article
Overview
Multi-factor Authentication (MFA) refers to having multiple types of evidence (or factors) to verify a user signing into a website, application, or other resource. These factors include, but are not limited to:
- Something the user knows: Password, Security Question, PIN
- Something the user owns: Computer, Mobile Phone, USB Key, Access Badge or FOB
- Something the user is: Voice Recognition, Fingerprint, Facial or Retina Scan
Additionally, a user's location or time of day can be used as factor for signing into a resource.
MFA Provider
An MFA provider is a service that supports MFA processes. Clearlogin is an MFA provider, it supports multiple types of MFA processes, and also has an MFA Authenticator app for Android and iOS. In addition to be an MFA provider, Clearlogin also supports the Cisco Duo MFA provider service.
Enable MFA in Clearlogin
- Log into the Admin Portal: https://admin.clearlogin.com
- In the left-hand navigation bar, browse to Security > Multi-Factor Authentication (MFA)
- Click on the MFA provider you wish to enable, and follow the below instructions for the provider you enable.

- If you have already enabled an MFA provider, click on the New MFA Provider button.

Expand to view the instructions for the MFA Provider you enabled.
- Clearlogin Authenticator MFA doesn't have any configuration steps. Just click on the Create button to enable it.
Clearlogin USB U2F (Universal 2 Factor) MFA requires a U2F USB device, and the latest version of Google Chrome or Mozilla Firefox. Apple does not currently support this standard with Safari, and the same is true with Microsoft Edge.
- Clearlogin USB U2F MFA doesn't have any configuration steps. Just click on the Create button to enable it.
For information on how to configure a USB key with Clearlogin, refer to the U2F USB Keys article.
- Clearlogin Guardian MFA doesn't have any configuration steps. Just click on the Create button to enable it.
For more information on how to use Clearlogin's Guardian MFA service, refer to the Guardian MFA article.
Before you enable Cisco Duo MFA, you will need to sign into your Duo admin portal and create an Auth API application:
- Sign into your Duo Admin Portal: https://admin.duosecurity.com
- Select Applications in the sidebar
- Click on Protect an Application and locate the entry for Auth API in the applications list.
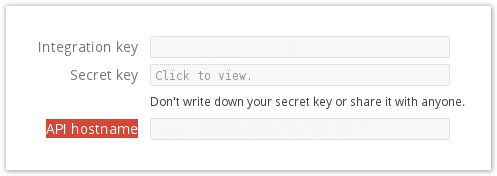
- Click Protect to the far-right to configure the application and get your integration key, secret key, and API hostname.
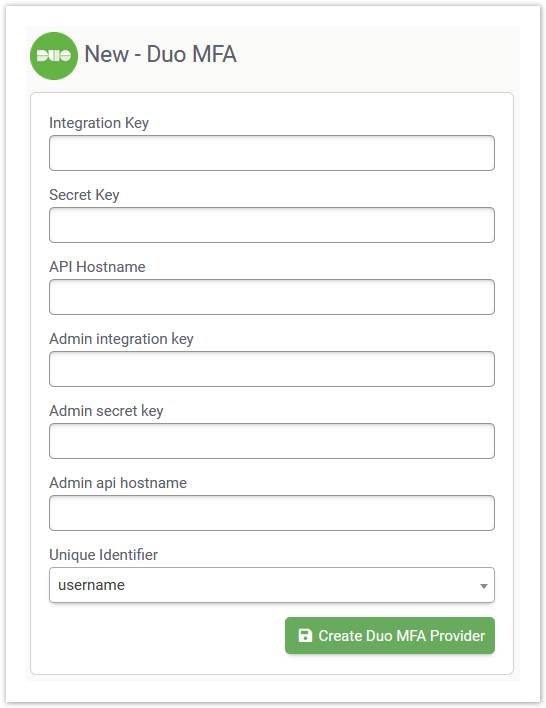
- In Clearlogin, click the DUO MFA button to enable the Cisco Duo MFA provider.

Enter the required configuration items and then click the Create button.
Integration Key < Paste this in from the Duo admin portal > Secret Key < Paste this in from the Duo admin portal > API Hostname < Paste this in from the Duo admin portal > Admin Integration Key Admin Secret Key Admin API Hostname Unique Identifier This is the unique identifier used to match your Clearlogin users to your Duo users. If you were to select username we will use the Clearlogin username (eg. admin@clearlogin.com would be 'admin')
- No labels